Pryvate CUG Technology
Engineered for Security and Auditibility
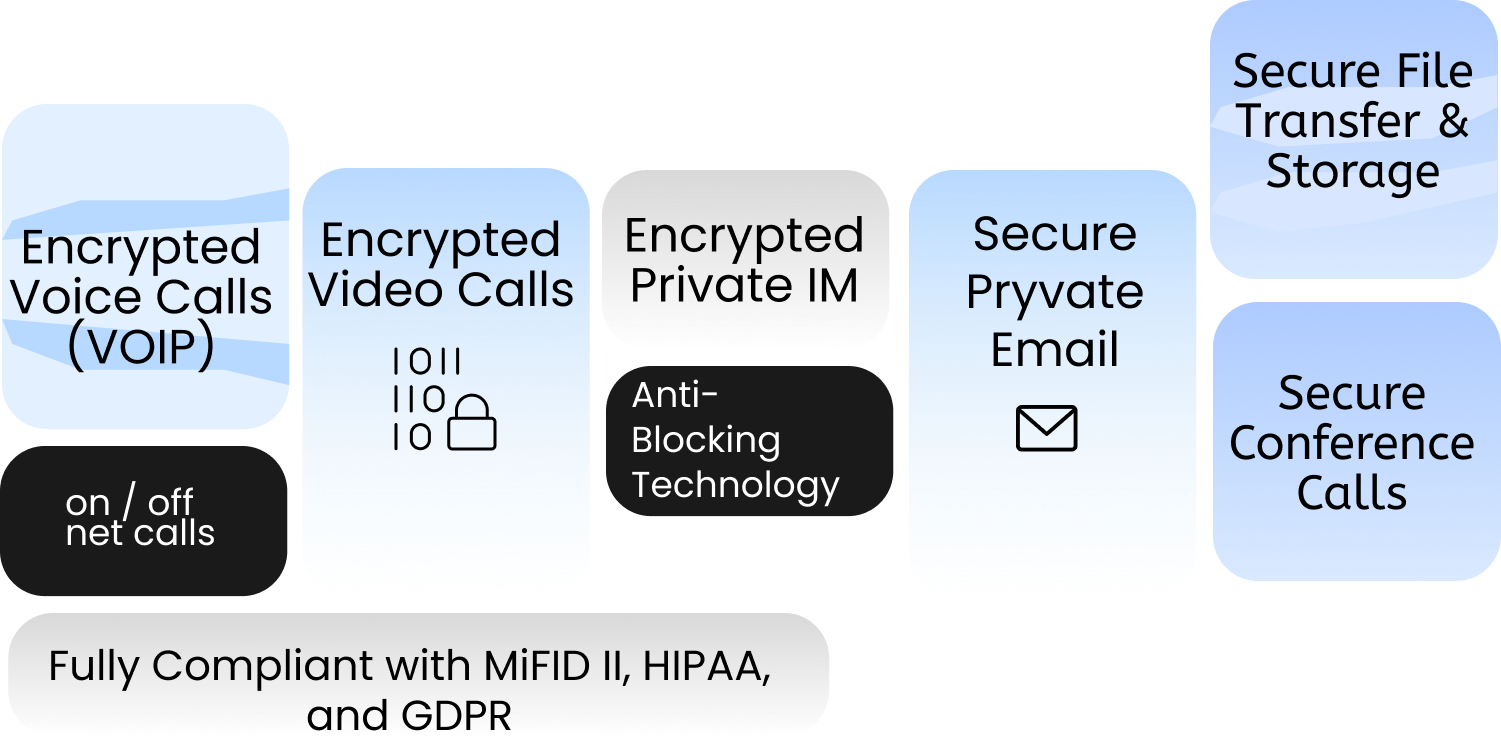
Closer Look at Pryvate Technology
“Pryvate is the industry pioneer for ultra-secure, feature-packed and compliant communication.”
Encrypted Voice Calls (VOIP)
Free, Secure Calls – Anytime, Anywhere
No roaming, no hidden fees. Connect via 3G/4G, LTE, WiFi, and more.
End-to-end encryption for every call. Keys are generated on your device, used once, and never stored.
No middlemen, no records. Your conversations stay private.
Encrypted video, unique keys for each call.
Private audio conferencing – hosted directly on your device.
Encrypted Private IM
Instant Messaging Encryption
Online conversations are at risk now more than ever – from hackers to government surveillance. Open WiFi and even password-protected networks can leave your IMs vulnerable. Secure your instant messages with encryption.
What is IM Encryption?
Off-The-Record (OTR) messaging ensures your IMs are fully encrypted, free from digital signatures, and impossible to monitor.
Encrypted Video Calls
Tailored Video Streaming Options
Different streams by region, media, device, or software. Adaptive streaming for optimal quality.
Secure Encryption – privacy guaranteed.
ZRTP Protocol ensures secure key exchange between VoIP endpoints.
Supports codecs like VP8, H263, MPEG4, H264, and more. Resolutions from QCIF to SVGA, adapting to your bandwidth and device capabilities.
Secure Pryvate Email
Secure Email, Seamless Integration
Secure any of your existing email addresses across platforms – Android to iOS. No need for new tech or retraining.
Supports 3G, EDGE, Wi-Fi, and more.
End-to-end encryption: Single-session keys for each email, never stored or known to Pryvate.
All communication is encrypted – TLS or RSA4096. RSA4096 public key encryption ensures unbreakable security between your app and server.
Secure File Transfer
Secure File Transfer with Pryvate
Transfer your important files worry-free with military-grade encryption. Pryvate ensures your data stays private, whether sent via email or shared through Dropbox, OneDrive, or Box – protected from hackers and competitors.
Need to encrypt large files? Pryvate has you covered. Encrypt files for delivery via CD/DVD/USB, automatically store them in-app, and let recipients easily decrypt with one click. Secure, private, and hassle-free.
Secure File Storage
Pryvate Secure File Storage
Protect your personal or corporate files with military-grade encryption. Whether on a device, PC, or shared via Dropbox or Box, Pryvate keeps your files safe from hackers and competitors. Files are encrypted and securely stored without traditional email risks.
Encrypted files can also be stored on external devices like USBs or DVDs. Decryption keys are never stored with the files, ensuring safety even if your device is lost or stolen.
Quantum Encryption
Pryvate Quantum-Resistant Voice & Video Encryption
Pryvate offers quantum-proof encryption for voice and video over IP using the CRYSTALS-Kyber algorithm – one of the world’s first secure implementations for quantum attacks. It provides robust encryption, compatible with previous versions and resilient to both quantum and classic attacks.
Key Features:
- Post-Quantum KEM in ZRTP: Enhanced ZRTP protocol to support post-quantum ‘key encapsulation mechanism.’
- Hybrid Encryption: Combines classic ECDH with post-quantum encryption for dual-layer security.
- ZRTP Fragmentation: Added packet fragmentation for enhanced communication reliability.
- Seamless Integration: Post-quantum ZRTP library integrated directly into Pryvate.
Secure Voice and Video Conference Calls
The technology behind the video conferencing solution is referred to as a ‘Selective Forwarding Unit’ (SFU) or ‘Selective Forwarding Middlebox’ (SFM).
The solution opens the path to conference sessions managed by a server that does not decode the media content.
This solution is the first SIP-based conferencing solution powered by a modern SFU server. It is compatible with open standards for managing group chatrooms and their participants.
Anti-Blocking technology
Pryvate works even where you’d least expect.
Pryvate’s Anti-Blocking Technology ensures uninterrupted, secure communication in regions with strict internet restrictions or censorship. Pryvate keeps your calls, messages, and data flowing securely and privately.
All your comms are truly private – not even Pryvate can ‘listen-in’.
Our advanced technology works seamlessly in the background, allowing you to connect with confidence, no matter where you are. With Pryvate, your communication remains protected and accessible, even in the most challenging environments.
